ISSA Proceedings 2002 – Risk, Vulnerability, And American Public Argument After September 11
No comments yet During June of 2001, President George W. Bush traveled to Europe to meet with allies during his first such foreign trip of his then young presidency. And for the press and the diplomats alike, different perspectives about risks and vulnerability to world ending threats were at the center of discussions. There was not a great deal of agreement about the ways in which such threats should be considered. The U.S. had formally announced it would not be signing the 1997 Kyoto Protocol, widely supported by leaders in Europe, and generally thought to require participation by the United States, the world’s largest emitter of Greenhouse gasses. The support for the Protocol elsewhere was based on a generally perceived threat of the long term catastrophic implications of global warning. For the vast majority of the developed world participants, action was needed to avoid a future catastrophe, in the words of the Ghostbusters, “of biblical proportion.” But President Bush was not prepared to act on this mere risk of catastrophe for our climate, given the magnitude of Kyoto’s provisions immediate effects on the US economy, and what he argued were the uncertainties of the current data available on climate. Under such conditions of uncertainty and hopefully time to act, the world should not base immediate action on our vulnerability to a disastrous future, however horrible that future might appear. And so wisdom would dictate, according to Mr. Bush, that “…the United States of America work within the United Nations framework and elsewhere to develop with our friends and allies and nations throughout the world an effective and science based response to the issue of global warming.” (New York Times, June 12, 2001, A12)
During June of 2001, President George W. Bush traveled to Europe to meet with allies during his first such foreign trip of his then young presidency. And for the press and the diplomats alike, different perspectives about risks and vulnerability to world ending threats were at the center of discussions. There was not a great deal of agreement about the ways in which such threats should be considered. The U.S. had formally announced it would not be signing the 1997 Kyoto Protocol, widely supported by leaders in Europe, and generally thought to require participation by the United States, the world’s largest emitter of Greenhouse gasses. The support for the Protocol elsewhere was based on a generally perceived threat of the long term catastrophic implications of global warning. For the vast majority of the developed world participants, action was needed to avoid a future catastrophe, in the words of the Ghostbusters, “of biblical proportion.” But President Bush was not prepared to act on this mere risk of catastrophe for our climate, given the magnitude of Kyoto’s provisions immediate effects on the US economy, and what he argued were the uncertainties of the current data available on climate. Under such conditions of uncertainty and hopefully time to act, the world should not base immediate action on our vulnerability to a disastrous future, however horrible that future might appear. And so wisdom would dictate, according to Mr. Bush, that “…the United States of America work within the United Nations framework and elsewhere to develop with our friends and allies and nations throughout the world an effective and science based response to the issue of global warming.” (New York Times, June 12, 2001, A12)
Even with the report of the National Academy of Science, there was not enough data to warrant action. “Yet the academy’s report tells us that we do not know how much effect natural fluctuations in climate may have had on warming. We do not know how much are climate could or will change in the future. We do not know how fast change will occur or even how some of our actions will impact it…(N)o one can say with any certainty what constitutes a dangerous level of warming, and, therefore, what level must be avoided.” (New York Times, June 12, 2001, A12). In other words, even in the face of huge potential vulnerabilities, we risk less if we wait until more study is completed on the climate.
Besides, President Bush was more concerned about other vulnerabilities facing the United States and other peace loving nations of the world. This threat was the continuation of the Antiballistic Missile Treaty of 1972, a “relic of the cold war” and a threat to those seeking answers to vulnerabilities of the 21st century. Mr. Bush explained to European listeners:” Part of the problem with the ABM Treaty is that it prevents full exploration of possibility. We’re bound by a treaty signed in 1972 that prohibits the United States from investigating all possibilities of how to intercept missiles…that we must fully explore in order to make sure that we have defensive capabilities necessary to prevent what I call blackmail…We must address the new threats of the 21st century if we’re to have a peaceful continent and a peaceful world. Those new threats are terrorism, based upon the capacity of some countries to develop weapons of mass destruction, and therefore hold the United States and our friends hostage….” (New York Times, June 13, 2001, p. 20).
The president’s differences in argumentative approaches did not escape even observers not always characterized as insightful. A puzzled journalist did not receive a direct answer from the president when asking “You say the scientific evidence isn’t strong enough to go forward with Kyoto. So then how do you justify your missile defense plan when there is even less scientific evidence that it will work?” (J. Glanz, The New York Times June 17, 2001, p. 1) Put another way, the President used a rather traditional calculation of risk when he refused to accept the Kyoto Protocol under current conditions – since the data is currently limited, we should not act. Potential harms should not lead us to believe that actions are warranted. Conversely, the President used traditional vulnerability arguments to justify his call to move forward with research on missile defense technologies. While the probability of terrorist actions is clearly uncertain, the magnitude of harm associated with even a single act of terror would justify immediately moving forward with research (Hynes, 1987).
The acts of September 11 changed dramatically the ways in which vulnerability and risk entered into American political discourse. Terrorist actions were no longer simply probabilities about which to posit policy alternatives, but real and vivid visual realities that could frame policy considerations. And it is in light of this new framing of arguments about future crises and harms that the current essay reviews arguments and institutions for the consideration of risks and vulnerabilities to catastrophic harm. The review will come in two sections: the first will review earlier analyses of risk and vulnerability as argumentative concepts; the second will observe how that framing has influenced the development of US government institutions designed for developing responses to perceived risks and vulnerabilities, especially institutions for Homeland Security.
1. Risk Society, Culture, and Argument
The concept of risk can be appropriately considered an essentially interactive one. Individuals derive understanding of risks based upon the nature of their own interpretations of messages about estimates about the chances of some harm befalling them. It is also the case that the interpretation of risks is framed by the institutions through which those risks are communicated and interpreted by individuals. In this instance we define institutions as a set of rules or conventions that structure interactions of agents subject to those rules (Di John, 2001).
Risk is not conceptualized in the same way by all communicators. The concepts used are framed by the institutions that dominate the concept of risk within various communication settings. Very often, the disciplinary perspective from which the consideration of risks originated provides the dominant view for interpreting this concept. And thus this section will consider four such perspectives – technical or scientific; sociological; anthropological or cultural; rhetorical or argumentative.
Risk as a scientific or technical concept. Risks and vulnerabilities within this perspective are essentially exercises in calculation, however complex that calculating exercise may be. “A simple, albeit ‘technocratic’ definition of that risk is the probability that an outcome will occur times the consequence, or level of impact, should that outcome occur” (Kammen and Hassenzahl, 1999, p. 3). “The risk and individual and/or a community faces is a function of the a) probability of a particular hazard and b) identified vulnerability minus c) the mitigation capacity of the community to handle the eventual realization of the disaster. “ Additionally, “Vulnerability captures the recognition that the extent to which people suffer from calamities of any kind (earthquakes, mudslides, etc) depends on both their likelihood of being exposed to shocks and hazards and their capability to withstand them….” (DiJohn, 2001, n.p.)
This type of analysis does indeed have a long history. Around 3200 B.C., a group of priests, the Asipu, in the Tigris-Euphrates Valley, established a methodology that included hazard identification, generation of alternatives, data collection and analysis, and report creation. And while the data did include signs from the gods, it did in many way approximate more contemporary scientific/technological approaches to risk and vulnerability assessment (Kammen and Hassenzahl, 1999, p.9). Tesh (2000) provides just such a contemporary risk assessment scenario within an environmental context.
A substance leaves a source (e.g., an industrial facility), moves through an environmental medium (e.g., the air), and results in an exposure (people breathe the air containing the chemical). The exposure creates a dose in the exposed people (the amount of the chemical entering the body, which expressed in any of several ways), and the magnitude, duration, and timing of the does determine the extent to which the toxic properties of the chemical are realized in exposed people (the risk). (p. 25)
Certainly these calculations take on meaning when they are given a clear context. The movement from individual to collective understanding of certain risks and vulnerabilities requires interpretation and subsequent consideration of public or private actions (seat belt laws are passed; individuals will only purchase vehicles that have side airbags; the governor of South Carolina will threaten to guard state borders to prevent the transportation of nuclear materials into the state; the Office of Homeland Security begins to make systematic ways to monitor attendance of foreign students in classes, perceiving that individuals on student visas may become a risk to public safety by participating in terrorist acts). And thus a variety of discipline based strategies have developed to give clues to ways in which those interpretations may happen. The second framework for interpreting risk is a social theoretical one.
Risk as a social theoretical construct.
Individuals’ interpretation and understanding or risk and vulnerability are integrally tied to social organizations within which individuals operate (Beck, 1992). The concept of the risk society is based on the seminal work of Ulrich Beck. For Beck the concept of risk is directly bound to the concept of reflexive modernization. “Risk may be defined as a systematic way of dealing with hazards and insecurities induced and introduced by modernization itself. Risks, as opposed to older dangers, are consequences which relate to the threatening force of modernization and to its globalization of doubt. They are politically reflexive” (Beck, 1992, p. 21). For Beck, modernity’s efforts to produce wealth (and to use wealth as a definition of a class based society) must now be accompanied by a systematic analysis of the social production of, and response to, risks. “Questions of development and employment of technologies… are being eclipsed by questions of political and economic management of the risks of actually or potentially utilized technologies – discovering, administering, acknowledging, avoiding or concealing such hazards with respect to specifically defined horizons of relevance. The promise of security grows with the risks and destruction and must be reaffirmed over and over again to an alert and critical public through cosmetic or real interventions in the techno-economic development.” (Beck, 1992, p. 19-20).
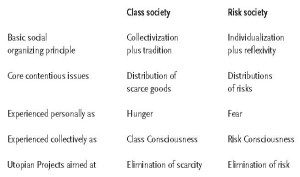
The comparison between traditional notions of modernity and Beck’s notion of reflexive modernity is found in the following table (Scott, 2000, p. 35):
Arguments about risk are for Beck an essential feature of general discourse, and social structures are developed or modified based upon the success with which they can help citizens make sense of risks. Risk analysis, ultimately, attempts to make the unpredictable predictable.
Risk as a cultural theoretical construct.
Douglas (1983, 1992) is the source of early work on risk as a cultural construct. And while later critics (Lash, 2000) would fault the conservative nature of that original perspective, the larger framework for seeing risk as a cultural phenomenon remained constant – risk is real to the extent that it is perceived to be so. Where there are perceived increases in the occurrences of risks, they are the result of influential social actors within a cultural setting claiming such is true. At least in the early work, with a focus on ecological risks, risks are constructed within the cultural borders of mainstream environmental analysis, and are intended to modify conventional cultural assumptions about dangers associated with change. Lash (2000) despairs that risk can be intelligently considered in a larger social context. Only by examining ways in which subsets of the larger culture – Lash’s cultural perspective – can there be an effective response to the larger risk society. Beck argues (2000) that the notion of a risk culture differs in degree rather than in kind from his own view of risk society. Nonetheless, the perspective underscores the notion that risks are translated into symbols, and that those symbols can be interpreted only within the culture in which those symbols are created and received.
Ironically, some of Douglas’ discussion of risk assessment and cultural theory springs from efforts to explain instances in which risk taking and risk analysis appear to defy traditional probability assessment. “We can give no account of the motives of men and women of the ancient Teutonic civilization of northern Europe, nor of the regions surrounding the Mediterranean where honour is a prime motivation, nor of the Plains Indians, nor of Islamic Fundamentalist groups … who take danger into their hands, for themselves as for their victims.” (Douglas, 1992, p. 41)
Risk as a rhetorical artifact.
Earlier work on the utilizing an argumentative perspective for actions rooted in risk and vulnerability has focused on public strategies for manipulating or modifying various public perceptions of risks and vulnerabilities. This activity is often guided by individual interpretations that tend to over or underestimate certain individual or societal risks (Hynes, 1987). Many of these arguments tend to follow predictable patterns – over or under estimating the chances of danger occurrence; over or underestimating the magnitude of potential societal damage, regardless of the probability that such events will occur; connecting or disconnecting with potential risks that have a societal reference (e.g., social overestimation of harms of nuclear power because of its connections to weapons, versus underestimation of harms of fossil fuel uses because of daily experiences which make such uses innocuous). Arguers do not benefit by directly confronting arguments from risk and vulnerability. They will benefit by recognizing at least two characteristics traditionally associated with interpretation of argument from risk.
First, individuals use certain heuristics to interpret risks for them – reflecting “common sense” assumptions that heart disease is less likely to confront an individual than say radiation from a nuclear power plant – or that prior to September 11, US citizens would be attacked on American soil. Thus arguments about vulnerability and risk are not likely to be subject to any rigorous probability judgment if the dangers are perceived by individuals as potentially applied to the individual.
Second, individuals can respond effectively to arguments about risk and vulnerability by using competing arguments for risk and vulnerability. These responses can be effective to the degree that arguers can discover a risk element that individuals perceive are similar to risks that are identified for avoidance – for example, coal burning releases radioactive materials when burned, and thus carries risks similar to those of other sources of radiation. (Hynes, 1987).
Rhetorical analysis of arguments from risk and vulnerability cannot be separated completely from the earlier perspectives. The technical interpretations of risk and vulnerability provide one possible focus of argument for decision makers and the public. Risk as a social construct frames an explanation of social structures and systems used to explain, minimize or highlight, provide reassurance that risks can be addressed. And of course risks must be interpreted. “The essence of risk is not that it is happening, but that it might be happening. Risks are manufactured, not only through the application of technologies, but also in the making of sense and by the technological sensibility of potential harm, danger, or threat … risks are being revealed in their construction” (Adam and von Loon, 2000, p. 2). Risk as cultural assumption focuses more on individual rather than social responses – individual responses often influenced by culturally shared use of symbols used to characterize risks rather than social systems used to explain, create, or mitigate them. These cultural assumptions are shared through the use of language systems. The rhetorical perspective looks to messages to determine ways in which cultural assumptions or social structures have been used to mediate meaning in language use about risk and vulnerability to new and continuing dangers.
In a sense this outlines the essential interdisciplinary nature of approach, and disciplinary desire to stake out ground in understanding ways in which individuals are governed by interactions with concepts of risk. In fact, much prior work considering risk have involved staking out disciplinary hegemony – the focus of later work in this area.
When hijacked American commercial airliners were crashed into the towers of the World Trade Center, the Pentagon, and a remote field in Pennsylvania, projections of risks to the U.S. from outside forces were exposed as real vulnerabilities. The ways in which these vulnerabilities were considered in public settings in coming months will be the subject of second section of this essay.
2. Applications post September 11
Not surprisingly, the immediate effects of attacks included dramatic efforts to make sense out of what was viewed as a change in risk calculations and perceptions – events predictable from a risk society perspective. “…the media which are being appropriate to make sense of risk provide risk sensibility and are thus involved both in the engendering and manipulation of risks, as well as their negotiation and displacement” (Adam and van Loon, 2000, p.23). And while there were profound changes in many aspects of American existence after September 11, there were equally predictable responses consistent with analytical, social, cultural, and rhetorical responses to risk and vulnerability. Two illustrations of these responses will be discussed.
Initiate the placement of risks and vulnerabilities into an analytical perspective.
It should not be surprising that initial responses to the attacks involved descriptions of strategies to analyze and maximize efforts to reduce probabilities for subsequent attacks. This would be accomplished by procedures approximately traditional risk/cost assessments. And thus on October 12, 2001, the General Accounting Office reported to the House of Representatives Subcommittee on National Security that specific risk management strategies should be undertaken to include specific clear and calculated elements. “Risk management principles acknowledge that while risk generally cannot be eliminated; enhancing protection from known or potential threats can reduce it. A good risk management approach includes three elements: a threat assessment, a vulnerability assessment, and a criticality assessment” (Decker, 2001, p. 1). The attacks would serve as a means of exposing the need to better analyze circumstances facing the United States, calculate the directions for greater protection, and reduce vulnerabilities to these threats now that we had been made aware of them. Calculations are now possible.
It became immediately apparent that such an analytical approach presumed an inventory of “vulnerabilities,” as well as a set of structures through which to create chances for interactions about those vulnerabilities. Did they exist? How would all the vulnerabilities be identified? How would we assign authority to assess responsibility for addressing vulnerabilities? How would priorities for addressing identified vulnerabilities be determined? And thus the next response to vulnerability required the creation of new social structures within which discourse about the predicted events would occur. Out of efforts to address these questions came the exploration of institutions that would frame social and rhetorical responses to risk and vulnerability.
Structured interpretation of vulnerabilities through the creation of institutions.
On September 20, 2001, President Bush announced the appointment of Thomas Ridge as the Director of Homeland Security, and Mr. Ridge’s responsibility for
“… coordinating federal, state and local efforts and leading, overseeing and coordinating a comprehensive national strategy to safeguard the nation against terrorism and respond to any attacks that may occur” (Walker, 2001, p.5).
We are here reminded that discourse about risk pushes focus of analysis from past to future – we speculate about what we might experience, based to a greater or lesser extent on what had already been experienced (Beck, 1992). And thus conversations about past or present events serve not necessarily as a prediction of the future. This was especially true in the context of dealing with heretofore unprecedented (at least within a U.S. context) ranging from physical/suicide attacks of September 11 to biological attacks (anthrax) to rumored chemical attacks via the use of crop dusters. And thus institutions were created which would depart from those historically associated with meeting domestic threats.
If, as noted earlier, institutions should be construed as a set of rules or conventions that structure interactions of agents subject to those rules, then review was soon required about the form that the office of Homeland Security would take. In its initial iteration, assessment of and interpretation of risks and vulnerabilities were to be accomplished largely informally. Rules were emergent, authority was shared over various governmental levels and among agencies and groups at each governmental level. Concerns about the communication of risk and vulnerability became the focal point of official discussions. These concerns manifested themselves in a number of ways – from whether there should be a priority for coping with certain risks and vulnerabilities, to whether Mr. Ridge did or did not have a responsibility of reporting to Congress at their request. Control over institutions and thus control over interactions was at core of change from initial informal structures for Homeland Security.
These initial actions did not prove to create institutions necessary to govern arguments about vulnerability and risk. What might be a sufficient reason for action in Washington may not be sufficient in one of the states. “And the chances of getting hit are one in 50 … and so the likelihood that the governor of New Hampshire is going to view the terrorism threat as the greatest threat, the biggest deal, is very unlikely because there are 49 other states to choose from” (Plummer and Carr, 2002, p. 1A).
The creation of a Homeland Security Advisory System in March of 2002 reflected a response to criticism that communication about general issues of vulnerability and risk (“there are rumors that someone is thinking about putting a bomb on the Golden Gate Bridge…”). And so the announcement of specific threat conditions (color coded) associated with threat credibility, threat corroboration, threat specificity, and threat gravity was an initial effort to codify ways that various public and private groups should interact about statements of risks and vulnerability.
Further, the call to create a Cabinet Level Office for Homeland Security, including restructuring of current formal institutions, reflects an association between arguments about risk and vulnerability, and the creation of institutions that frame those interactions. Major and minor disputes about structures for such an office arise in large part over control of the origination of arguments – ranging for questions of exclusion of the Federal Bureau of Investigation and the Central Intelligence Agency from direct control by this new authority to exclusion of the scientists at the Lawrence Livermore Labs. Beck would predict greater specificity over time to structure governmental approaches to these new risks. Hynes would predict that the success of the development of these institutions will pivot on competing arguments about greater or lesser vulnerabilities associated with these varied institutional structures.
After September 11, a variety of areas of potential risk and vulnerability heretofore seen as improbable gained both public and governmental recognition. These areas have brought to bear social structures which allow arguments to be framed that both given sense to prior events, and allow coherent conversations and assessments of the future. Arguments take a predictable form, reflecting social and cultural assumptions of risk and vulnerabilities, as well as rhetorical strategies which give understanding of how individuals can manage their own predictions and assessments of these risks.
REFERENCES
Adam, B., and van Loon, J., (2000) Introduction: repositioning risk. In B. Adam, U. Beck and J. van Loon. The risk society and beyond. (pp. 1-31). London: Sage
Beck, U. (1992) Risk Society. London: Sage
Beck, U., (2000). Risk society revisited, In B. Adam, U. Beck, and Van Loon, J. The risk society and beyond. (pp.211-229) London: Sage.
Bush, G., Address to a joint session of congress and the American people, retrieved June 20, 2002 at http://www.whitehouse.gov/news/releases/2001/09/20010920-8.html.
Decker, R., (2001) Homeland Security, GAO-02-150T, Washington: General Accounting Office.
Di John, J., (2001) An institutionalist political economy perspective of risk and vulnerability. Retrieved June 15,2002, from http://www.proventionconsortium.org/files/highrisk/DiJohn.pdf
Douglas, M. and Wildavsky, A., (1983) Risk and Culture. Berkeley: U of California
Douglas, M. (1992) Risk and Blame. London: Routledge.
Hynes, T. (1987) Risk, Vulnerability and policy analysis: implications for public argument. Wenzel, J. Argument and critical practice Annenberg: SCA
Kammen, D. and Hassenzahl, D., (1999) Should we risk it? Princeton: Princeton University
Lash, S., (2000) Risk culture, Adam, B., Beck, U. and Van Loon, J. The risk society and beyond. London: Sage pp.47-62.
Mitchell, A. (2001) A nation challenged: domestic security. New York Times Section B, p. 5. Retrieved March 18, 2001, from Lexis-Nexis Academic Universe.
Plummer, D. and Carr, R. (2002) U.S. still donning security armor, Atlanta Journal Constitution, Retrieved May 17, 2002, from Lexis-Nexis Academic Universe.
Scott, A., Risk society or angst society, (2000) Adam, B., Beck, U. and Van Loon, J. (2000) The risk society and beyond. (pp.35-46). London: Sage.
Tesh, S. (2000) Uncertain hazards, Ithica: Cornell University.
Walker, D., (2001) Homeland security; challenges and strategies in addressing short- and long-term national needs, GAO-02-160T, Washington: GAO.
You May Also Like
Comments
Leave a Reply